Addresses
A blockchain address is a string of digits and characters that can be shared with anyone who wants to send you money. Here’s an example of a Hathor blockchain address:
HNzKKHLvubxNLXyfMsvxNzVxeZw5MyAdaf
Hathor assigns multiple addresses to its users, much like Ethereum and Bitcoin wallets do. Every time an address is used we generate a new one as the suggested address to be the next used one, even though all previous addresses are still valid and can be used in as many transactions as the user wants. Technically, there is nothing wrong with using the same address over and over again, but using a new address for every transaction creates an additional layer of privacy protection.
For Ethereum, users need to have ETH on the address they want to send tokens from. Hence, most just concentrate all their funds in a single address as they don't want to have ETH in multiple addresses. That's very different from exchanges, where each user is assigned an address from a single wallet.
A straightforward way to check this strategy of using multiple addresses is through Hathor's Desktop Wallet. As that wallet uses the gap limit default value, i.e., 20, it starts with 20 available addresses to be used in transactions. Every time an address is used, a new one is generated. This way the wallet ever keeps a sequence of 20 distinct addresses in memory.
The Hathor address is derived from the public key through the use of one-way cryptographic hashing. A “hashing algorithm” or simply “hash algorithm” is a one-way function that produces a fingerprint or “hash” of an arbitrary-sized input. Cryptographic hash functions are used extensively in Hathor: in Hathor addresses, in script addresses, and in the mining Proof-of-Work algorithm.
Addresses Pattern: The addresses of the Hathor’s mainnet and testnet follow a pattern. All addresses of the mainnet start with the letter H (P2PKH address) or h (P2SH address) and addresses of the testnet start whether W (P2PKH address) or w (P2SH address).
To be more precise, in Hathor, public-key cryptography is used to create a key pair that controls access to HTR. The key pair consists of a private key and - derived from it - a unique public key. For the public key derivation, an elliptic curve-based mathematical function is employed.
Hence, the Hathor address generation process starts with generating the private key, applying the elliptic curve math function to turn that into a public key, and finally, generating a Hathor address from the public key through a hash function. The relationship between private key, public key, and Hathor address is shown in the figure below.
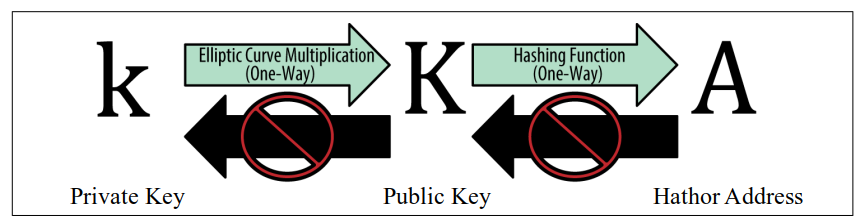
Private key, public key, and Hathor address.
The address is used to receive funds, and the private key is used to sign transactions to spend the funds. Then, when spending HTR, the current HTR owner presents her address and a signature (different each time, but created from the same private key) in a transaction to spend those HTR.